|
|
|
|
|
Flaws In Your PC: The Top 5 Most Vulnerable Applications When Working Online
Published Nov 29, 2012
|
depend on vulnerabilities in popular applications to penetrate computers, and target operating systems, browsers, office packages and music players to deliver their malicious payload.
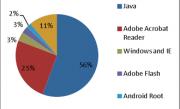
Kaspersky Lab has uncovered the five main types of vulnerable applications targeted by exploits. According to a Q3 2012 report on malware activity, Java vulnerabilities are used in more than half of all attacks. Updates for the software are installed on demand rather than automatically, increasing the lifetime of vulnerabilities. Java exploits are easy enough to use under any version of Windows and, with some additional work by cybercriminals, as in the case of Flashfake, cross-platform exploits can also be created. This explains why cybercriminals are especially interested in Java vulnerabilities.
Attacks via Adobe Reader rank second, accounting for a quarter of all blocked attacks. The popularity of exploits for Adobe Reader is gradually declining due to a relatively simple mechanism that ensures their detection, as well as automated updates introduced in the latest versions of the software. Exploits targeting vulnerabilities in the Windows Help and Support Center, as well as various Internet Explorer (IE) flaws, accounted for 3% of all attacks.
For several years now cybercriminals have been constantly on the lookout for errors in Flash Player. According to Kaspersky Security Network, in Q3 of 2012 the Top 10 vulnerabilities included two entries for Adobe Flash. Our Top 5 is rounded off by exploits targeting devices running under Android OS. They are mainly aimed at ‘jailbreaking’ devices to provide any software – genuine or malicious – with full access to the memory and features of a telephone or tablet.
“Today, the Internet is a very aggressive environment. Virtually any site may turn out to be infected and visitors with vulnerable applications on their computers can easily fall victim to cybercriminals,” commented Sergey Novikov, Head of Global Research and Analysis team, EEMEA, Kaspersky Lab. “Cybercriminals primarily target electronic accounts or confidential user data, expecting to be able to turn this information into cash. They use all available methods to deliver malware to the user’s computer, and exploits just happen to be one of the most popular methods.”
Applications with vulnerabilities targeted by web exploits, Q3 2012
“We strongly advise our users to keep the software installed on their computers up to date and use the latest protection measures such as the Advanced Exploit Prevention technology integrated into our new user products,” added Sergey Novikov.
The new Advanced Exploit Prevention technology implemented in Kaspersky Internet Security 2013 and Kaspersky Anti-Virus 2013 prevents and blocks exploit activities. The main functionality of the technology includes:
- control over the launch of executable files from applications (including web browsers) where vulnerabilities are detected, or from applications not designed to launch executable files (Microsoft Word, Excel etc.);
- checking for any signs of malicious exploit behavior if executable files are launched;
- monitoring the activities (following links, recording other processes, etc.) of applications where vulnerabilities have been found.
To ensure protection is as effective as possible, all information (the list of applications known to contain vulnerabilities, control over the launching of files by applications) can be updated.
Posted by
VMD - [Virtual Marketing Department]
|
|
|

